NX Monorepo – Debug login flow with production auth
Problem to Solve
You want to log in to http://localhost:4200 using the production authentication flow
inside an NX monorepo setup, without mocking auth or bypassing guards.
Context / Keywords
- NX monorepo
- Angular frontend
- NestJS AuthGuard
- JWT login via URL
- Debugging using browser
- Production auth in local environment
Expected Behavior
When accessing the local frontend with a valid production login token:
[http://localhost:4200/decrypt?login=](http://localhost:4200/decrypt?login=)<JWT>&path=/admin
The application should:
- Consume the
logintoken - Authenticate the user
- Redirect to:
[http://localhost:4200/admin](http://localhost:4200/admin)
Actual Behavior (Problem)
Instead of a single redirect, the application keeps redirecting and repeating the login token inside the path parameter, producing URLs like:
[http://localhost:4200/decrypt?login=](http://localhost:4200/decrypt?login=)<JWT>&path=/admin?login=<JWT>,/admin?login=<JWT>,/admin?
This results in:
- Exponentially growing URLs
- Redirect loops
- Inability to reach
/admin
Reproduction Steps
- Open a normal browser window
- Navigate to:
[http://localhost:4200/decrypt?login=](http://localhost:4200/decrypt?login=)<JWT>&path=/admin
- Observe repeated redirects and URL growth
Temporary Workaround (What Actually Works)
✅ Open an Incognito / Private window
[http://localhost:4200](http://localhost:4200)
➡️ The application successfully redirects to:
[http://localhost:4200/admin](http://localhost:4200/admin)
Why Incognito Works
Incognito mode starts with a clean browser state.
In a normal browser window, the following values may persist between attempts:
setEncryptedTokensaveUserapplicationOrigin- stored redirect
path loginAs/ login-related query params
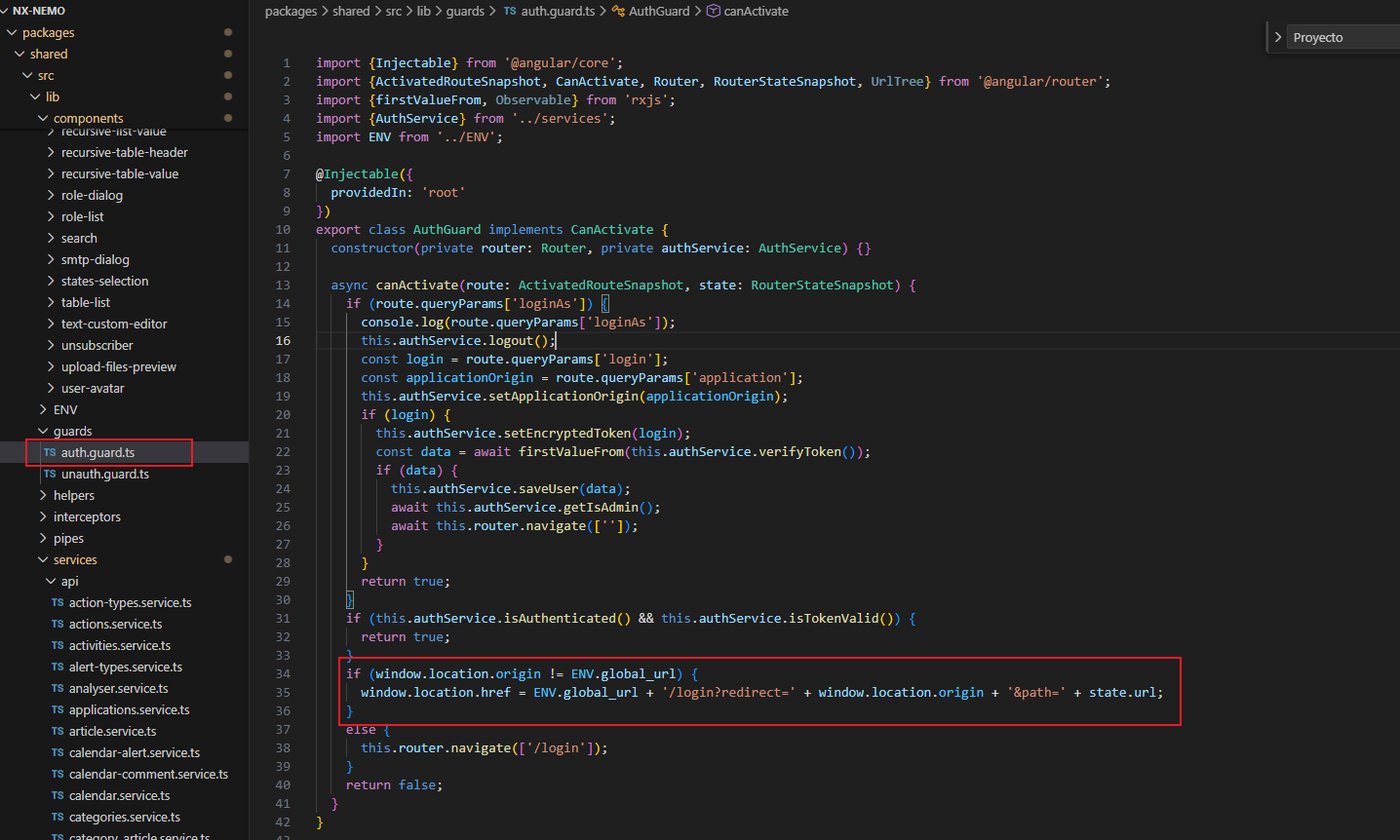
Because of this, AuthGuard is triggered multiple times with polluted state, causing
the same URL (including login) to be repeatedly appended to path.
In Incognito:
- No localStorage
- No sessionStorage
- No cookies
- No previous redirect state
➡️ AuthGuard executes once with a clean state, and the flow completes correctly.
Root Cause Analysis
This issue is not a browser bug.
The real causes are:
- AuthGuard performs login side effects
- Token verification
- User persistence
- Redirect logic
- URL parameters (
login,path) are not cleaned after consumption state.url(including query params) is reused as a redirect path- AuthGuard is executed again before the URL is cleaned, causing redirect loops
In short:
AuthGuard mixes authentication checking and login execution, which leads to repeated redirects when using JWT login via URL.
Code Review (Relevant Parts)
Routing logic for production environment
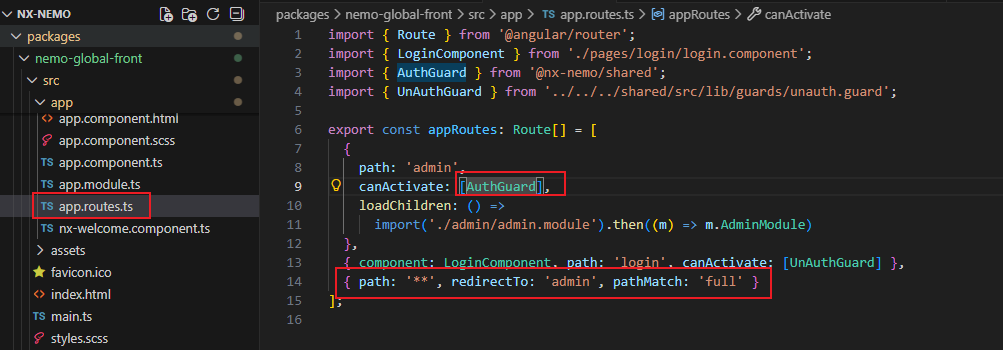
AuthGuard implementation
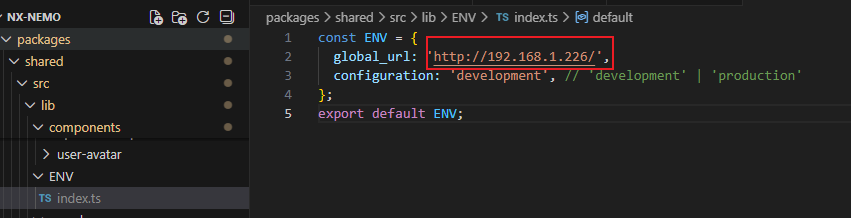
Global login URL configuration
Key Takeaways
- AuthGuard should only decide access, not perform login
- Login tokens passed via URL must be consumed once and removed
- Redirect paths must never include login-related query parameters
- Incognito success indicates state pollution, not token issues
Recommended Improvements (Future Work)
- Move login/token consumption to a dedicated
DecryptComponent - Keep AuthGuard responsible only for:
isAuthenticatedisTokenValid
- Clean URLs using
replaceUrl: trueafter login - Avoid using full
state.url(with query params) as redirect path
Summary
Using production authentication inside a local NX monorepo environment can expose hidden redirect and guard execution issues.
The infinite redirect loop was caused by AuthGuard handling login logic combined with uncleaned URL parameters, not by JWT or browser behavior.
Incognito mode worked because it reset all persisted authentication state.